What you will need:
- Santoku – Alpha 0.1 (or later)
- AFLogical OSE (already installed in Santoku)
- An Android device (with adb enabled)
AFLogical OSE Background
AFLogical OSE was released in December 2011 and is now hosted on GitHub. The app provides a basic framework for extracting data from Android devices using Content Providers and then saves the data to the SD Card of the device including:
- Contacts
- Call Logs
- SMS
- MMS
- MMS Parts
- Device info
AFLogical OSE has been successfully tested on Android 1.5 through 4.1 (Jelly Bean) and across many non-standard Android devices.
Installing and running AFLogical OSE
First, let’s get a terminal prompt in the correct directory by navigating to Santoku –> Device Forensics –> AFLogical OSE.

To install AFLogical OSE, connect your Android device over USB and if you are running Santoku CE in a VM, make sure you pass the USB connection through. You can run the following command to verify Santoku can communicate with your Android device:
adb devices
which should return your device serial number.
santoku@santoku-vm:/opt/santoku/af-logical$ adb devices
* daemon not running. starting it now on port 5037 *
* daemon started successfully *
List of devices attached
01653EF81C00510F device
If you do not see something similar to this, you need to resolve this issue first.
Next, you need to push AFLogical OSE to your Android device:
For Santoku 0.4 and later
Install the application to your device:
aflogical-ose
You should receive a success message as follows:
634 KB/s (28794 bytes in 0.044s)
pkg: /data/local/tmp/AFLogical-OSE_1.5.2.apk
Success
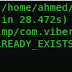
Starting: Intent { cmp=com.viaforensics.android.aflogical_ose/com.viaforensics.android.ForensicsActivity }
Press enter to pull /sdcard/forensics into ~/aflogical-data/
Again, if you receive an error, you need to resolve the issue.
Next, on your target device, select the data you want to extract and click “Capture”:

In your AFLogical-ose terminal window in Santoku, press enter to pull the data from your SDCard to the location “~/aflogical-data”. Santoku will automatically pull all the data recovered from your device to that location.
To view the data, open a terminal window and type:
$ cd ~/aflogical-data/
$ ls
20131028.1039
The data is stored under a folder labeled with the date and time of the acquisition. In this example, it was 2013-10-28 at 10:39 local time.
You can then open the “~/aflogical-data” directory in Nautilus and browse any images as well as the extracted data (such as contacts, call logs, mms/sms, and device info) in CSV format:
For Santoku 0.1 to 0.3:
First, install the application to the device:
adb install AFLogical-OSE_1.5.2.apk
You should receive a success message as follows:
santoku@santoku-vm:/opt/santoku/af-logical$ adb install AFLogical-OSE_1.5.2.apk
574 KB/s (28794 bytes in 0.048s)
pkg: /data/local/tmp/AFLogical-OSE_1.5.2.apk
Success
Again, if you receive an error, you need to resolve the issue.
Run AFLogical on your Android device:
To run AFLogical OSE, , navigate to it through Applications –> AFLogical OSE:

Then select the data you want to extract and click “Capture”:

AFLogical OSE will then save the extracted data on the SD Card of the device. You can now uninstall AFLogical OSE with the following command:
adb uninstall com.viaforensics.android.aflogical_ose
which will close the app (if still running) and remove from the device:
santoku@santoku-vm:/opt/santoku/af-logical$ adb uninstall com.viaforensics.android.aflogical_ose
Success
Pull and examine the extracted data:
AFLogical OSE creates a folder on the SD Card called forensics and then a subfolder with the date and time of the extraction. The easiest way to copy the data to Santoku is with the recursive “adb pull” command:
adb pull /mnt/sdcard/forensics
which will extract all data under that directory (so, if you reuse a removable SD Card, you might have multiple subfolders with data). Here’s some example output (truncated for space):
santoku@santoku-vm:/tmp$ adb pull /mnt/sdcard/forensics
pull: building file list...
pull: /mnt/sdcard/forensics/20120912.0741/Contacts Phones.csv -> ./20120912.0741/Contacts Phones.csv
pull: /mnt/sdcard/forensics/20120912.0741/SMS.csv -> ./20120912.0741/SMS.csv
pull: /mnt/sdcard/forensics/20120912.0741/MMSParts.csv -> ./20120912.0741/MMSParts.csv
pull: /mnt/sdcard/forensics/20120912.0741/MMS.csv -> ./20120912.0741/MMS.csv
pull: /mnt/sdcard/forensics/20120912.0741/CallLog Calls.csv -> ./20120912.0741/CallLog Calls.csv
pull: /mnt/sdcard/forensics/20120912.0741/info.xml -> ./20120912.0741/info.xml
pull: /mnt/sdcard/forensics/20120912.0741/Photo0284.jpg -> ./20120912.0741/Photo0284.jpg
11 files pulled. 0 files skipped.
499 KB/s (893180 bytes in 1.746s)
You can then open the directory in Nautilus and browse any images as well as the extracted data (such as contacts, call logs, mms/sms, and device info) in CSV format:






0 comments:
Post a Comment