Viber Introduction
Viber Application is a cross-platform application that allows users to do voice calls, send messages and share images with their contacts using windows, IOS, Android, Blackberry, Symbian and windows phone devices
Tools Used In this Analysis
Santoku 0.5 , Wireshark , Tcpdump , Dalvik debug monitor , SQLite3, Android SDK Manager , Android Studio , Android AVD
Emulator Device info:
Nexus 5 (4.95”, 1080 x 1920: xxhdpi)
Android 4.4.2 – API Level 19
CPU: ARM (armeabi-v7a)
Memory: 1024
Internal Storage: 200 Mib
SD card: 200 MiB
Viber Artifacts during Installation/Usage
Applied Method: (Search & Compare)
After installing Viber on the emulator machine
Started pulling / directory from the emulator to the local machine to get the Artifacts of installed Viber.
After pulling / directory and by using search command “Find, Locate, grep”
To identify the directories viber installed in
Installing viber create new directories & subdirectories in
Ex.
Directories: .android, app lib
Subdirectory: /data/data/com.viber.voip
The Main location of viber installation is “/data/data “
But also viber creates some files in
/mnt
/cache
/storage/sdcard
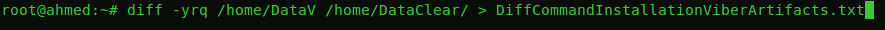
So by pulling those Directories from a clear emulator then from emulator containing viber and another one after uninstalling viber. to local machine
And Applying “diff” command to compare the three Folders Output We Found
This is a sample of the Artifacts created by installing viber
DataV “Directories Pulled from emulator with installed Viber”
Viber Artifacts after Uninstallation
By applying the same Method
This is a sample of the Artifacts Left by viber after Uninstalling
DataUnV “Directories Pulled from emulator with Uninstalled Viber”
Just to confirm this method
DataV (viber installed), DataUnV (viber Uninstalled), DataClear (Clean emulator)
Different incomplete Method to Get the Artifacts
Using Droid-box
After Suffering fixing python errors to install the droidbox-sandbox tool
The sandbox collected 0 logs for the viber application
Even when I run some activity on viber
Another Trial with Droidbox, trying to run it with older versions of android 4.1.2
The sandbox collect is working but the viber application crashes even when I try an older viber versions
The output of this trial is attached “installation.txt”
Droidbox output is a file json
And from my opinion it needs a python developer to extract understandable data from it J
Memory Process acquisition
Viber Process Analysis
Trial One J
Tool used: MemFetch
MFetch List file attached for Viber Process (mfetch.lst)
To determine files open by the viber process
Command used “lsof -p 697”
Trial Two J
Procmem command Show memory breakdown for selected processes
Including file memory usage and stack, heap
Trial Three J
Small Part for Viber Memory Analysis
Tools used: Dalvik debug monitor, Eclipse Memory Analyzer
Memory Heap File Attached (com.viber.voip)
This is a Report Sample
Problem Suspect 1
One instance of "android.graphics.Bitmap" loaded by "<system class loader>" occupies 1,324,864 (10.83%) bytes. The memory is accumulated in one instance of "byte[ ]" loaded by "<system class loader>".
6,328 instances of "java.lang.Class", loaded by "<system class loader>" occupy 1,547,304 (12.65%) bytes.
Biggest instances:
- class android.text.Html$HtmlParser @ 0xb2c0adf0 - 126,632 (1.04%) bytes.
class java.lang.ref.FinalizerReference @ 0xb2aff010 - 123,496 (1.01%) bytes.
Trial Four J
DD
Tried to capture viber Process memory using “dd” Command
From /mem Directory
It Works but can’t analyzie the output using Volatility, Error “No suitable address space mapping found”
Whatever tried to change the profile of volatility but with no success
KDGBScan Output nothing
Attempt reverse engineering data format of at least one non-self-explanatory artifact created by the program.
Using Sqlite3
After pulling Viber Databases from emulator to Local machine
root@ahmed:/home/ahmed/database# sqlite3 viber_data
SQLite version 3.8.2 2013-12-06 14:53:30
Enter ".help" for instructions
Enter SQL statements terminated with a ";"
sqlite> .tables
android_metadata phonebookcontact sync_data note: non-self-explanatory
blockednumbers phonebookdata vibernumbers
calls phonebookrawcontact
sqlite> select* from android_metadata;
en_US
sqlite> .headers ON
sqlite> select* from android_metadata;
locale
en_US
sqlite>
It is not encrypted and the output means local language used.
Another non-self-explanatory artifacts by viber
root@ahmed:/home/ahmed/database# sqlite3 viber_messages
SQLite version 3.8.2 2013-12-06 14:53:30
Enter ".help" for instructions
Enter SQL statements terminated with a ";"
sqlite> .tables
adx messages note: non-self-explanatory
android_metadata messages_calls
applications participants
backgrounds participants_info
blocked_data public_messages_extras
conversations purchase
group_conversations_extras stickers
kvdata stickers_packages
sqlite> select * from adx
...> ;
1|Launch|1434103141341
2|PlaceCall|1434015073223
3|Send_1to1_message|1434015110750
sqlite> .headers ON
sqlite> select * from adx
...> ;
_id|event_name|last_tracked
1|Launch|1434103141341
2|PlaceCall|1434015073223
3|Send_1to1_message|1434015110750
sqlite>
The output is not encrypted.
Network Traffic (Viber Application)
Tools: Wireshark, Tcpdump, Network Miner
Network traffic Captured File Attached (NetworkTraffic (Viber).pcap)
Extracting a PCAP file From Emulator
Running wireshark with root specifies the Emulator interface eth0
Starting viber activities on emulator to speed the traffic operation
Save the Output.
Another method to capture network traffic
Using tcpdump
Running command inside the emulator shell
tcpdump -w /sdcard/Traffic.pcap host 10.0.2.15
Running command from host machine
adb shell tcpdump -w /sdcard/Traffic.pcap host 10.0.2.2
Pulling the Output file
Adb pull /sdcard/Traffic.pcap /home/ahmed
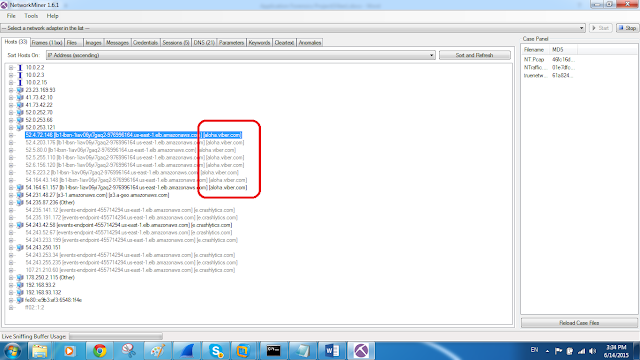
Using Network Miner to analyze the Output File
Note: Viber Servers Connections established
Running whois command to identify the connected Servers
















0 comments:
Post a Comment