The Volatility software may be downloaded from here- https://code.google.com/p/volatility/downloads/list
It also comes pre-installed with Backtrack 5 R3, which I am presently using. Demo Tutorial Selecting a Profile For performing analysis using Volatility we need to first set a profile to tell Volatility what operating system the dump came from, such as Windows XP, Vista, Linux flavors, etc.
We have a memory dump with us and we do not know what operating system it belongs to, so we use the imageinfo plug-in to find this out.
I have also explained how to take a memory dump using Helix ISO in the end of the document for the people who might be new to it.
Type ./vol.py imageinfo –f
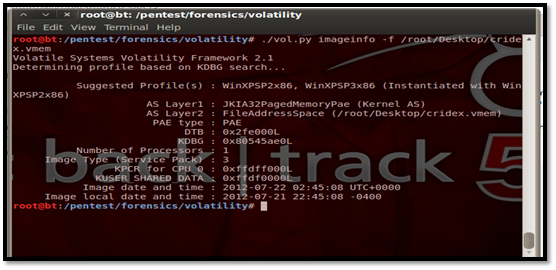
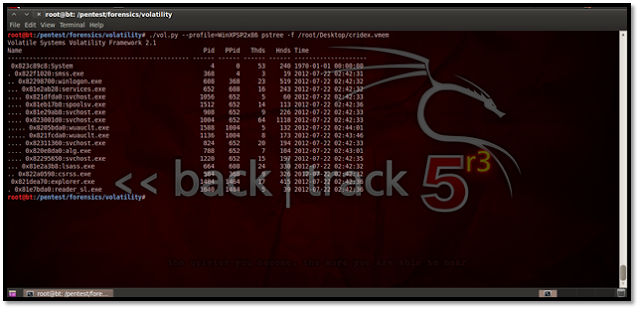
Viewing Running Processes This plug-in gives us the option to view all running process on the particular system during which the memory dump was taken. Let us see how to use it:
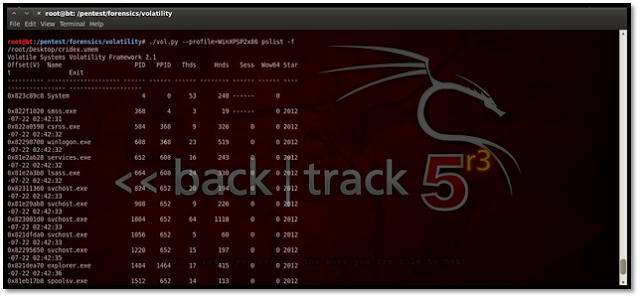
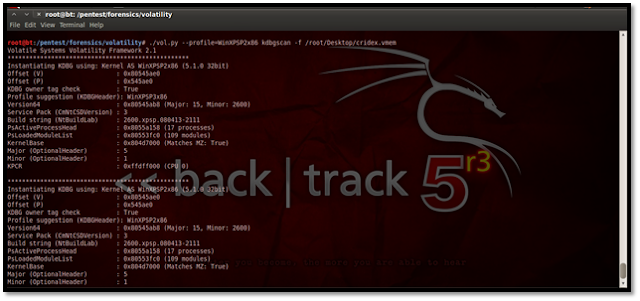
The above screenshot shows a clear view of all the processes running during the memory dump. Using Kdbgscan This particular plug-in is designed to positively identify the correct profile of the system and the correct KDBG (kernel debugger block) address. It simply scans for KDBG header signatures linked to the profiles in Volatility. This is mainly helpful in clearing up confusions which might be caused if the Pslist plug-in not showing any processes in the process list. This may happen if a KDBG with an invalid PsActiveProcessHead pointer is found earlier in a sample.
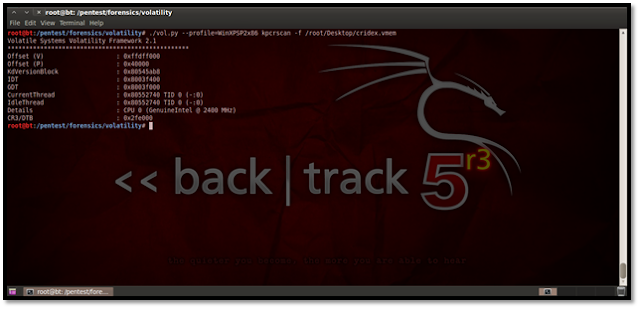
Using Kpcrscan This plug-in is used to scan for KPCR (Kernel Processor Control Region) structures. A KPCR is a data structure used by the kernel to store the processor-specific data. Kpcrscan searches for and dumps potential KPCR values. Each processor on a multi-core system has its own KPCR. In the screenshot below we can see the details of the processor, which is a single-core processor.
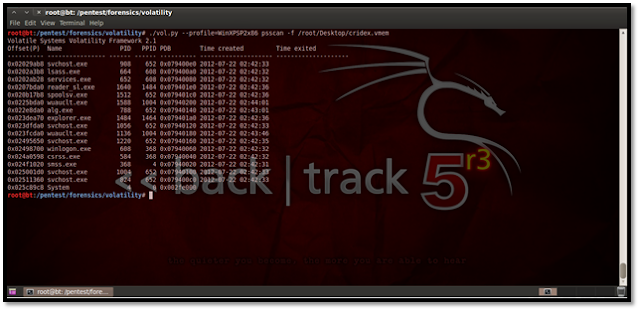
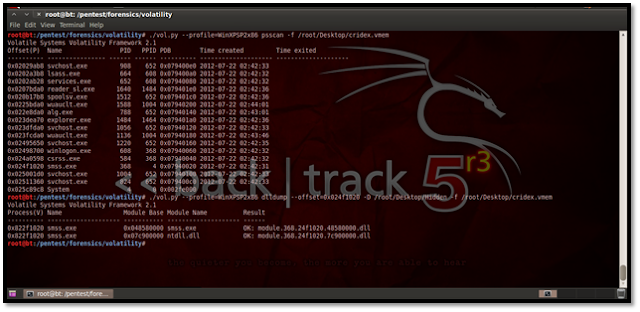
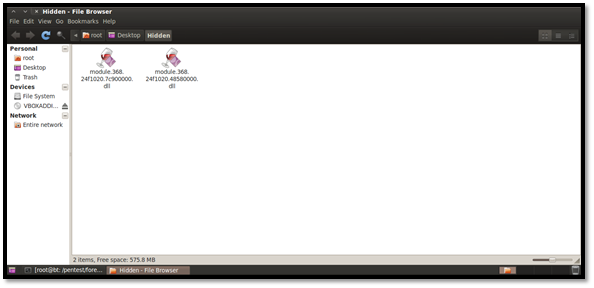
Using Psscan for Malware Analysis This plug-in is mostly used for malware analysis and scanning rootkit activities. It scans for inactive, hidden and unlinked processes by a rootkit/malware. Here’s how we do it:
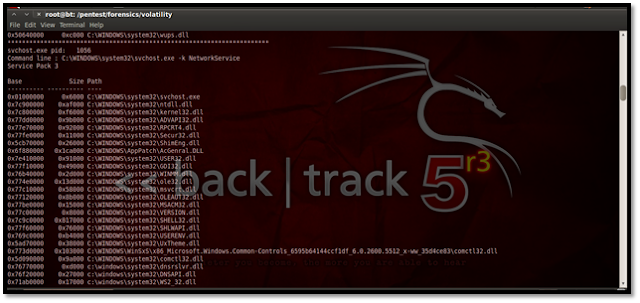
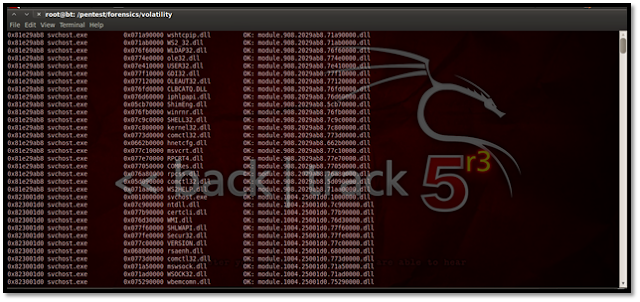
Using Dlllist To display the DLLs for all currently running processes or a particular process we use this plug-in.
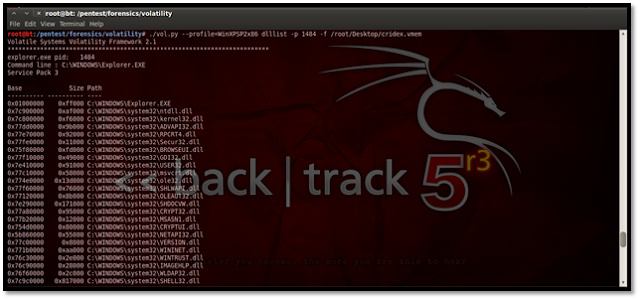
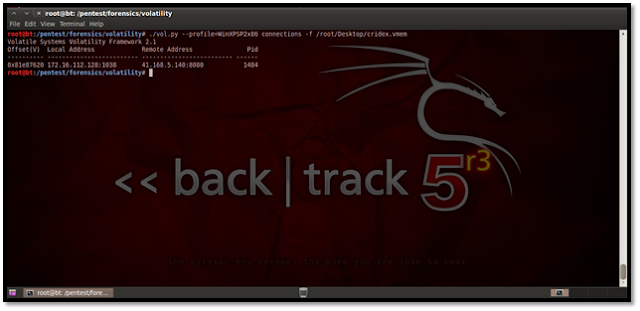
For listing the DLLs for a specific process, suppose we list here the DLLs of explorer.exe, which has the process id 1484. The process id may be found using the pslist plug-in.
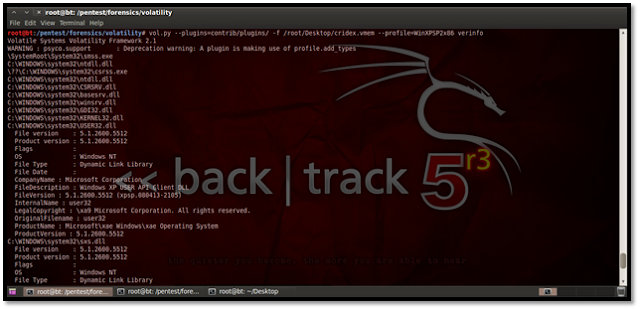
Using Dlldump We can dump all the DLLs for further forensic analysis using the command:
./vol.py –profile=WinXPSP2x86 dlldump -D
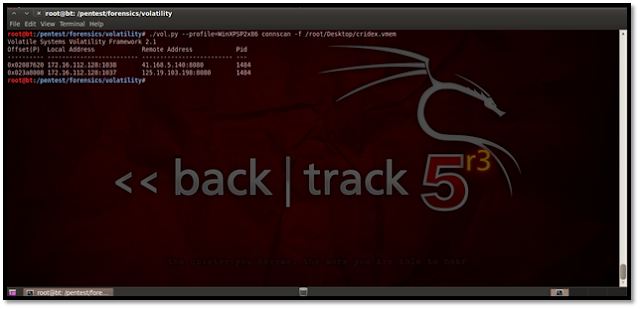
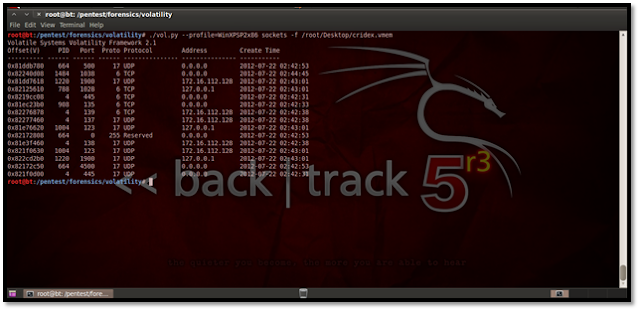
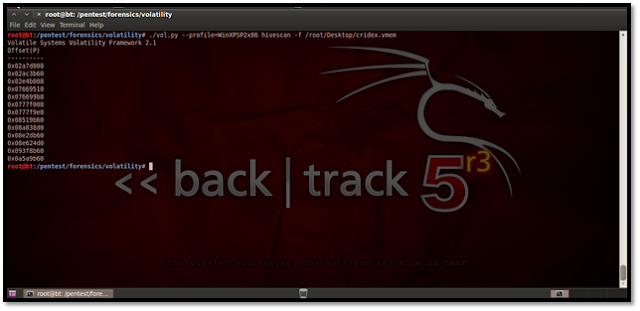
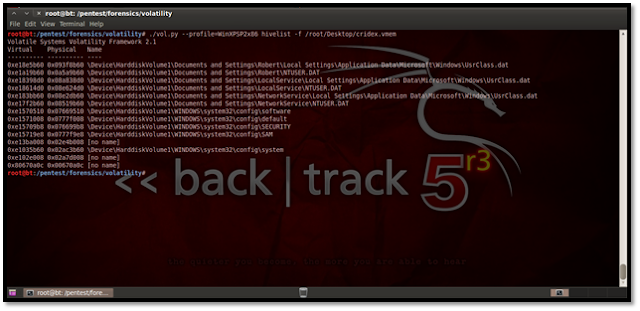
http://lorgor.blogspot.in/2010/11/volatility-memory-forensics-iiusing.html
http://www.computersecuritystudent.com/FORENSICS/VOLATILITY/lesson2/index.html
https://code.google.com/p/volatility/wiki/CommandReference21
https://code.google.com/p/volatility/wiki/VolatilityIntroduction




0 comments:
Post a Comment